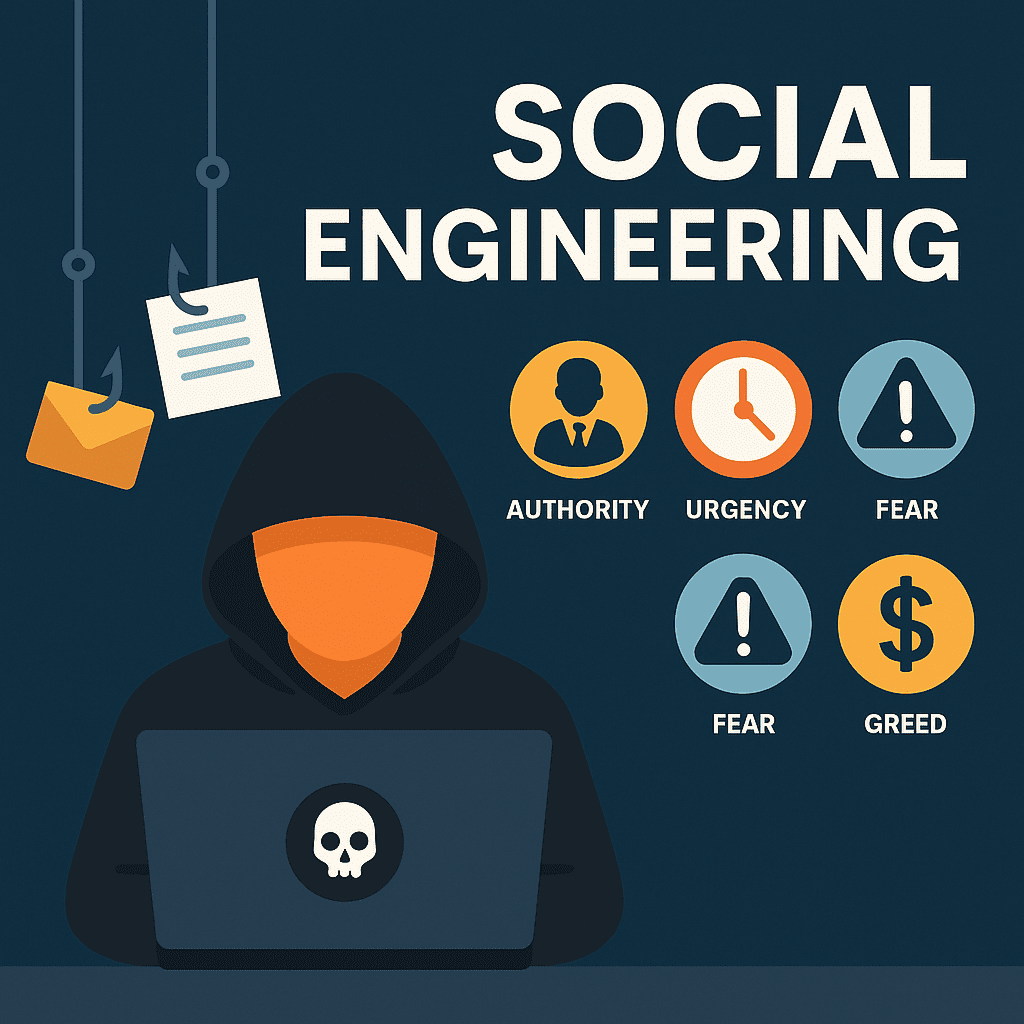
Watch Out for These Sneaky Phishing and Social Engineering Attacks
Phishing and social engineering attacks are no longer just clumsy emails with bad grammar. Today’s cybercriminals are using AI, voice cloning, and sophisticated psychological tactics to target your business—and they’re not going after your firewall… they’re going after your people.
Why Social Engineering Works—and How to Defend Your Business
You’ve locked down your network. You’ve deployed antivirus and firewalls. But cybercriminals aren’t always looking to break your systems—they’re looking to trick your people.
Welcome to the world of social engineering.
Case Study: How a client transformed their practice with I.T.WORKS! Managed IT Services
In the world of oral and maxillofacial surgery, precision and reliability aren’t limited to the operating room — they extend to every part of the practice, including technology. For our client, a forward-thinking medical practice in Massachusetts, outdated IT infrastructure was holding them back. That is, until they partnered with I.T.WORKS!, a Cape Cod-based Managed Services Provider (MSP) committed to helping businesses like theirs thrive through proactive, long-term IT solutions.
Tackling the Hidden Challenges of Network Monitoring
Your business’s lifeline resides in its network. Ensuring a healthy and secure network is crucial for seamless communication and operational efficiency. This necessitates proactive identification of issues and optimization of performance through continuous network security monitoring.
How to Successfully Leverage AI in Your Business
Artificial intelligence (AI) can help organizations like yours gain an edge in today’s highly competitive business landscape by increasing efficiency, productivity and profitability. You can improve customer service, enhance marketing efforts, optimize inventory management, streamline sales processes and more.
How to Prioritize Your Technology Gaps
Today’s technology-based businesses must deal with multiple issues, including cyberthreats, head-to-head competition and regulatory compliance. Hence, keeping your technology infrastructure up to date is critical, and a technology audit is the best place to start.
Why You Should Prioritize Your Technology Gaps
Technology is an unavoidable component of most businesses these days, helping them achieve their goals and vision. However, if you are not cautious, technological flaws could allow cybercriminals to access your network and cause harm to your company. Technology auditing is the solution to this problem.
A technology audit can assist you in better understanding and identifying gaps in your organization’s security, compliance and backup postures. But if you don’t have a background in IT, the results of a technology audit can be confusing. You may be overwhelmed by the number of items that need to be refreshed or replaced, and you may not know where to start.
Having a managed service provider (MSP) by your side can help you avoid these stumbling blocks. An MSP can provide you with a prioritized list of the most urgent to least urgent gaps, allowing you to decide how to proceed and allocate funds.
Don’t Overlook These 3 Technology Budget Categories
Technology is essential for any modern business such as yours, but it’s easy to focus solely on routine services that keep the lights on. This could lead you to miss crucial budget categories, leaving you scrambling when unanticipated needs arise.
Keep reading to learn about three critical budget categories — projects, refreshes and accidents/incidents — that are often overlooked and how they can affect your business.
4 Common Technology Budgeting Mistakes
Budgeting for technology can be tricky. On the one hand, you want to be ready for anything, but you also don’t want to overspend and waste valuable resources.
We’ve compiled a list of the most common technology budgeting mistakes you should avoid. Keep reading to learn more about those oversights.
Tech Budgeting 101 for Small Businesses
It’s important to understand that in today’s highly digitized environment, technology shouldn’t be an afterthought. You need to have a clear and well-defined IT budget since an unanticipated technology issue in the middle of the year could cause trouble.
4 (EASY TO DO TODAY!) Preventable actions to ensure technology is safe over the Long Labor Day Weekend
Increase your peace of mind PRIOR the long Labor Day weekend. Ensure business technology is prepared, then relax knowing your business has done everything to avoid and stay ahead of cyber security threats.
You have decided to hire a Managed IT Services Provider and pay top dollar for IT help, yet still have computer problems?
A business locked into an IT contract yielding mediocre results is a problem. Unfortunately, many businesses may choose to accept less than perfect results (sometimes, they don’t know what results they should even expect).
When was the last time you CHANGED your PASSWORD? It’s probably time!
Team members are trying to get so much done, so fast, and the fear of losing time because of a forgotten or changed password causes delays. These changes will help deter what could potentially be a major security breach.
What are the Benefits of a Businesses Having a Firewall?
Firewalls enhance businesses online security and protect unauthorized internet connections. A well configured firewall will protect computers against spam email, malicious links, viruses, pop ups, worms and ultimately hackers.
Why it is necessary for Businesses to purchase Paid Enterprise Grade software.
Paid Enterprise Grade software will protect business operations and client information, to keep your business safe, reliable and productive.
Why is it important to update, upgrade, and patch business IT?
Skipping Regular Updates, Upgrades and Patches results in decreased performance and renders business IT exposed.
Mitigate business IT vulnerabilities every day, just by staying current.
A disciplined approach to business IT mitigates vulnerabilities every day.
Are your team members trained to avoid cybersecurity threats? Cybersecurity is a human error.
I.T.WORKS! mitigates employee risk by staying ahead of it, and training both clients and their team members on best practices.
Did your backup work last night? Seriously, does your business verify backup for recovery purposes?
Each business must assess the timeframe and costs of acceptable downtime and make informed decisions evaluating the cost and recovery times.
Why do businesses accept technology that doesn’t work?
Businesses need to understand that technology CAN work consistently, reliably, and productively.
Just Because Technology is WORKING, Does Not Mean it’s Safe, Reliable or Secure.
There is RISK in not doing things the right way. Just because something works, does not always mean it is safe, reliable, or secure.
.
What are the Important Fundamentals of Data Backup?
Having a conversation about backup is actually a multi-layered conversation. There is no such thing as a standard backup for every business. There are multiple layers of choices, with issues spanning from a lost file to a catastrophic event or ransomware.
Why Small and Medium Sized Businesses Need Cyber Insurance.
Simply taking out a cyber insurance policy won’t protect your business from a cyber-attack. To properly protect your organization and your clients, businesses need a proactive comprehensive risk management plan.
Environmental Operating Solutions, Inc. (EOSi)
Sometimes clients need to end relationships, even when everything promised was delivered and expectations were exceeded. Read a case study from EOSI, a past client.
How often does your business create service tickets for business technology issues?
The benefits of CONSISTENTLY WORKING TECHNOLOGY offer fewer issues (i.e. “tickets”), less reactive time, increased work time, efficiency for your team, and less stress. Time is spent working instead of hours wasted on the frustrations of technology problems.
Should employees manage small business IT needs or leave it to the IT professionals?
Small businesses typically make do with basic technology when opening a new business. Funding constraints cause employees or owners to commonly manage their IT issues. However, as businesses mature and acquire additional employees and systems, they are faced with the additional complexities of business technology.
How Can Businesses Protect and Safeguard Confidential Client Information?
If your business deals with proprietary and sensitive data, this data is the fundamental reason your business exists and makes money. If you are not able to protect this information, it can cost you clients and your business. Utilizing best practices will be the best way to protect your clients and business IT.
Why Should Businesses Utilize Multi-Factor Authentication (MFA)?
MFA may not be convenient nor easy, but do not bypass safety policies for ease of use, these strategies are in place for a reason, PROTECT YOURSELF AND BUSINESS IT FROM SECURITY THREATS.
Business IT Support Companies are NOT created equal.
Diversity builds stability. We are exposed to all types of technical challenges and know how to solve business technology problems.
Should Employees Manage Small Business IT Needs or leave it to the IT Professionals?
When employees are involved in resolving IT issues, they are not focusing on core competencies nor completing their work to full potential, in addition to supplementary tasks burdening workload.
Insurance Companies are Requiring Cybersecurity Business Continuity Plan (BCP)
The comprehensive Business Continuity Plan (BCP) details how to reestablish office productivity, enterprise data and software so that key business operations are restored and includes strategies for managing IT disruptions to networks, servers, and computers due to cyberattack, fire, flood, theft, hardware failure, pandemic, etc.
Spencer Hallet Plumbing & Heating Case Study
I.T.WORKS! business model is the perfect IT solution, their responsiveness, positive can-do attitude, technical savvy, keeps my business running perfectly. I have never worked with a better run company, no matter the trade.
Why Healthcare Technology NEEDS to be HIPAA Compliant
HIPAA compliance is the law, for the health community, there is no choice. If rules aren’t adhered to, those that do not conform could face hefty fines and legal ramifications, hence why these protocols are so important to implement.
Productivity Thrives with Consistently Working Technology
Increase Employee and Business productivity, reap the benefits of your technology always working, and focus on your business core competencies.
Should businesses be aware of increased cybersecurity attacks with the invasion of Ukraine?
The answer is overwhelmingly, YES. It is always important for businesses to be cautious, however right now with the increase in cyberattacks due to the invasion, the reality is that your business may not be a direct target, but become an indirect target.
Why it is necessary for Businesses to purchase Paid Enterprise Grade software?
Paid Enterprise Grade software will protect business operations and client information, to keep your business safe, reliable and productive.
High-Level Cybersecurity Risk Assessment
This form is to help your business start a conversation around cybersecurity. While this form is not technical in nature, (I.T.WORKS! would probably have potentially 400 questions because we need to be incredibly granular), it is a high-level introduction around efforts that can be made to engage this conversation.
How Do You Protect Business From Ransomware?
Unfortunately, ransomware is easy to acquire, simple to deploy and is a massive problem for businesses. We all are very well-aware that many businesses need to take cybersecurity more seriously. But the elusive question continues to remain – HOW DO YOU PROTECT BUSINESS FROM RANSOMWARE??
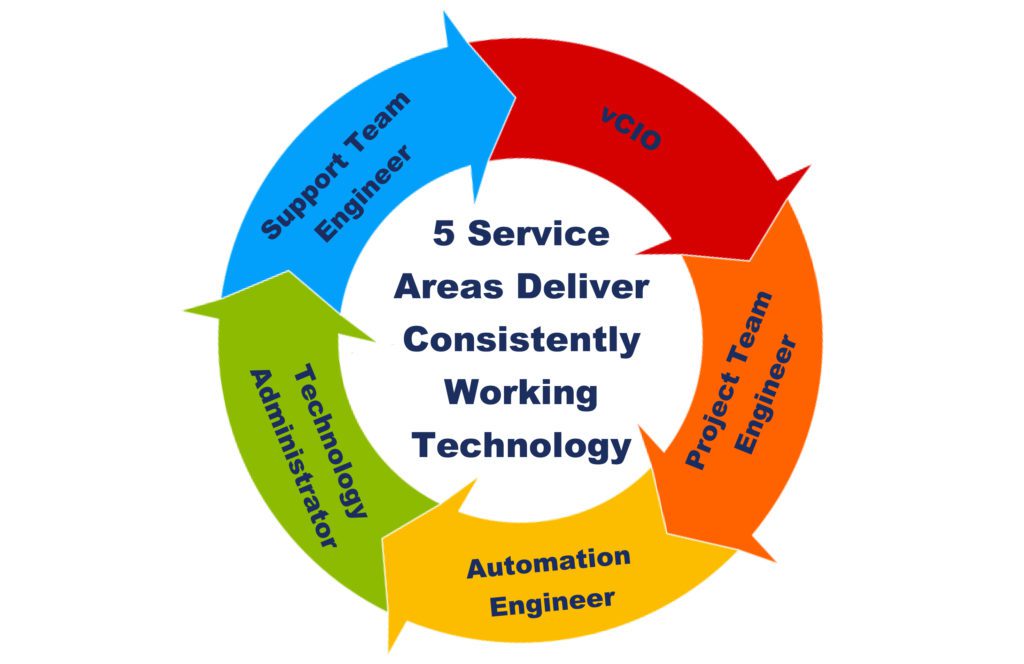
The Best Technology is CONSISTENTLY WORKING TECHNOLOGY
Our low-ticket levels speak volumes to the fact that proactive maintenance is occurring. Consistently working technology removes business IT frustration. We unequivocally understand the true cost of keeping systems consistently up and running, and the expertise, technology and manpower required to make it happen. We also understand that downtime is enormously expensive for clients.
Change your Passwords
Please take the advice of an IT solutions company that truly cares. Do not bypass safety policies for ease of use, they are in place for a reason, PROTECT YOURSELF AND BUSINESS FROM SECURITY ISSUES.
How to best stay ahead of vulnerabilities such as Log4j
Unfortunately, not all vulnerabilities make the news like Log4j. This is why it is incredibly important to stay ahead of IT issues, with proactive maintenance, applying all updates, upgrades, and patches to best protect business IT.
Prepare Business Technology for the Holidays 🎁
Improve your peace of mind BEFORE the holiday to ensure business technology is ready, then enjoy the festivities confidently knowing your business has done everything to avoid and stay ahead of cyber security threats.
Why the healthcare industry is consistently the target of ransomware attack
Choosing the correct IT Services Company is vital, it is not just the technology, but also the people and process in place that increase your cybersecurity protection. If an IT Services Company is continuously buried in service tickets, they will not have the time, nor discipline, to apply timely patches and other vital actions – and this will leave a business vulnerable.
DO NOT CLICK, Advice from a Technology Services Provider
Do not bypass safety policies for ease of use, they are in place for a reason, PROTECT YOURSELF AND BUSINESS FROM SECURITY ISSUES.
Berkshire Facial Surgery Case Study
As I reflect on our relationship with I.T.WORKS! over the years, I am struck by the foresight and execution of the I.T.WORKS! team in constructing a network that would meet my needs not just 10 years ago but today as well.
The Cape Cod Foundation Case Study
Thank you to I.T.WORKS! and your dedication to always getting it right for The Cape Cod Foundation. We are continuously up and running and making a difference in our community, always ready for what is next on our horizon, knowing our technology will support us 100%.
Benefits of Consistently Working Technology
Fewer Service Tickets, Less Reactive Time, Increased Efficiency for Team Members, Reduced Security Risks and Superior Business Performance. Ultimately Increasing Business Profit Margins.
New, Add Move & Change
We unequivocally understand the true cost required to providing a solid and reliable IT infrastructure and the importance of keeping systems consistently up and running, and the expertise, technology and manpower required to make it happen.
Resetting Expectations of IT Service Providers
When clients are new with us, they can’t comprehend technology consistently working. Our current clients will ONLY accept technology that is ALWAYS working. We love this change in perception of what is acceptable.
Frequently Asked Questions
I.T.WORKS! Answers Tough Information Technology Questions. We offer PEACE OF MIND & BETTER RESULTS! Technology is an investment when it consistently operates and can be depended upon, because technology drives business.
Password Strength Test
Cyberattacks have evolved out of Mom’s basement and now operate as a global network of sophisticated cyber criminals. A complex, memorable password will significantly help secure your online identity.
5 Benefits of Hiring a Managed Services Provider (MSP) for Small and Medium Sized Businesses
We see profit margins increase consistently with working technology. Employees are actively working on their core competencies and that drives business profitability.
How Your IT Support Company Can Help Keep Technology Healthy
Check in with your IT Support Company, just as you would attend your regular physicals!! Listen to the advice they give, and keep your technology healthy.
What to Expect from Microsoft Windows 11
Microsoft Windows 11 expected release date is October 20, 2021. Security plays a big part in this new version, while cleaning up some of the clutter of the old interface.
Cybersecurity. What You Need To Know, But Don’t Want To Hear
Technology must be protected. It’s comforting to believe that you can be 100% protected, and if you’re told it is possible, it’s simply not true. If 100% safe technology existed, everyone would be doing it! However, you can make it much harder for a cyber-attack to happen…
Business IT Support Services Cost of Ownership
I.T.WORKS! has a different pricing plan than other business IT support services. We have a unique all-inclusive flat rate that includes all projects and services. What does ALL-INCLUSIVE include? EVERYTHING!…
Start Planning NOW with IT Providers for Windows 11
I.T.WORKS! will enthusiastically be available to implement Microsoft Office changes for all clients that desire the new version and have the software to support it, as it offers the highest security for your technology. We have the technology and technical talent to do it, and the best part, it is standard with our service offering.